Platform Engineering as a Product
Treat infrastructure as a product, developers as customers, and governance as code
🧭 1. Why ?
In today’s digital-first landscape, speed, scale, and secure delivery are table stakes — yet many organizations still operate with fragmented infrastructure, disjointed pipelines, and inconsistent developer experiences. These silos slow delivery, increase cognitive load, and introduce operational risk.
This blog lays out a comprehensive Point of View (POV) on how to design and implement a unified, opinionated Platform Engineering capability — inspired by Amazon’s internal model but customized for today’s cloud-native, multi-cloud, and hybrid realities.
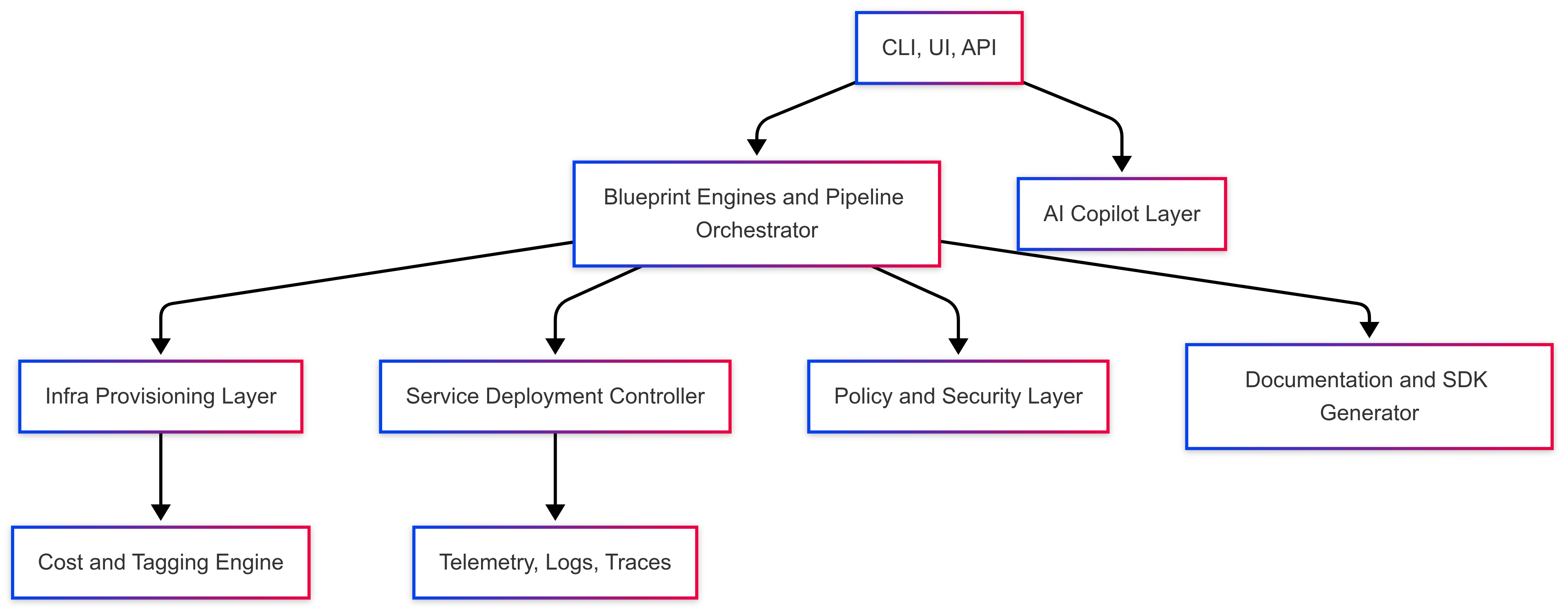
At the heart of this platform is a “You build it, you run it” philosophy. It enables engineering teams to build, deploy, and operate services autonomously, while giving platform teams the ability to embed security, compliance, and observability by design — not as an afterthought.
This platform is not a tooling initiative. It’s a strategic capability that delivers:
-
Developer self-service from code to production
-
Infrastructure as product — abstracted but customizable
-
Embedded compliance via policy-as-code
-
Scalable DevOps automation that reduces operational burden
-
A single, consistent developer experience via API, CLI, and UI
🧩 2. Current State Analysis
Across multiple digital-first organizations, the challenges tend to follow a common pattern — regardless of tech stack, industry, or scale.
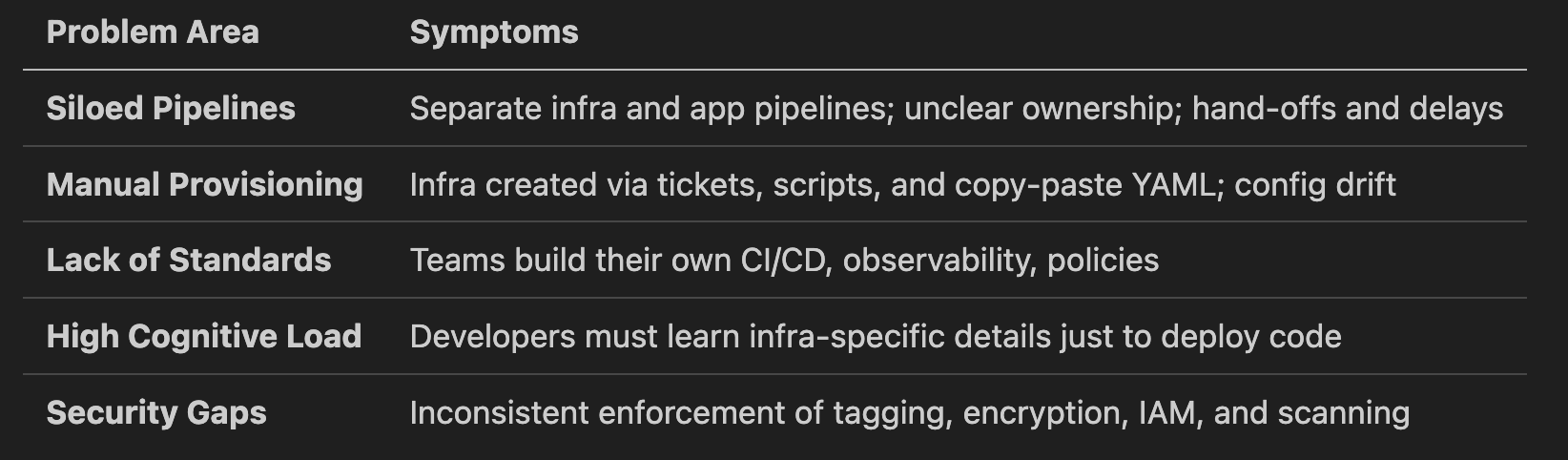
These issues introduce avoidable risk, reduce delivery velocity, and raise the total cost of ownership — particularly when scaling across teams or managing hybrid/multi-cloud environments.
Current State Friction Map
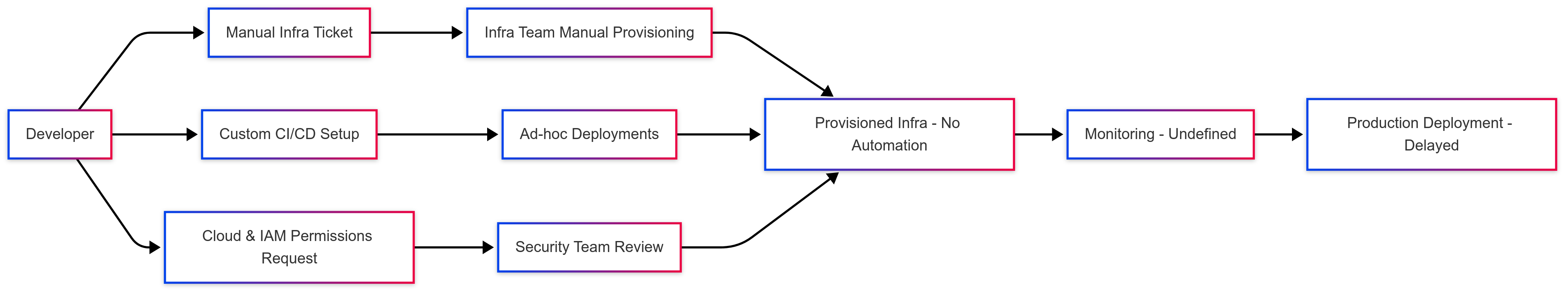
❌ Outcome: Drift, duplication, delays, and developer fatigue.
💡 3. Vision and Design Philosophy
The proposed platform capability delivers a code-first, API-driven internal developer platform (IDP) that empowers developers to:
-
Provision infrastructure without needing to understand cloud-specific primitives
-
Use golden templates (blueprints) for services, CI/CD, and observability
-
Get built-in compliance through policy-as-code, not after-the-fact reviews
-
Work autonomously via self-service interfaces (API, CLI, UI)
-
Operate in a world where everything is defined, versioned, and managed via code
🔑 Guiding Principles
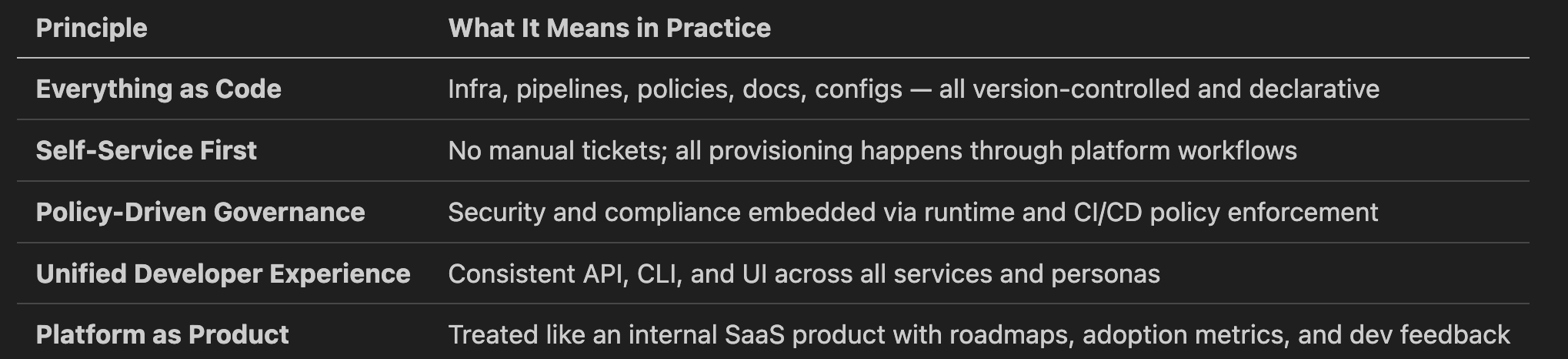
Target Operating Model Overview
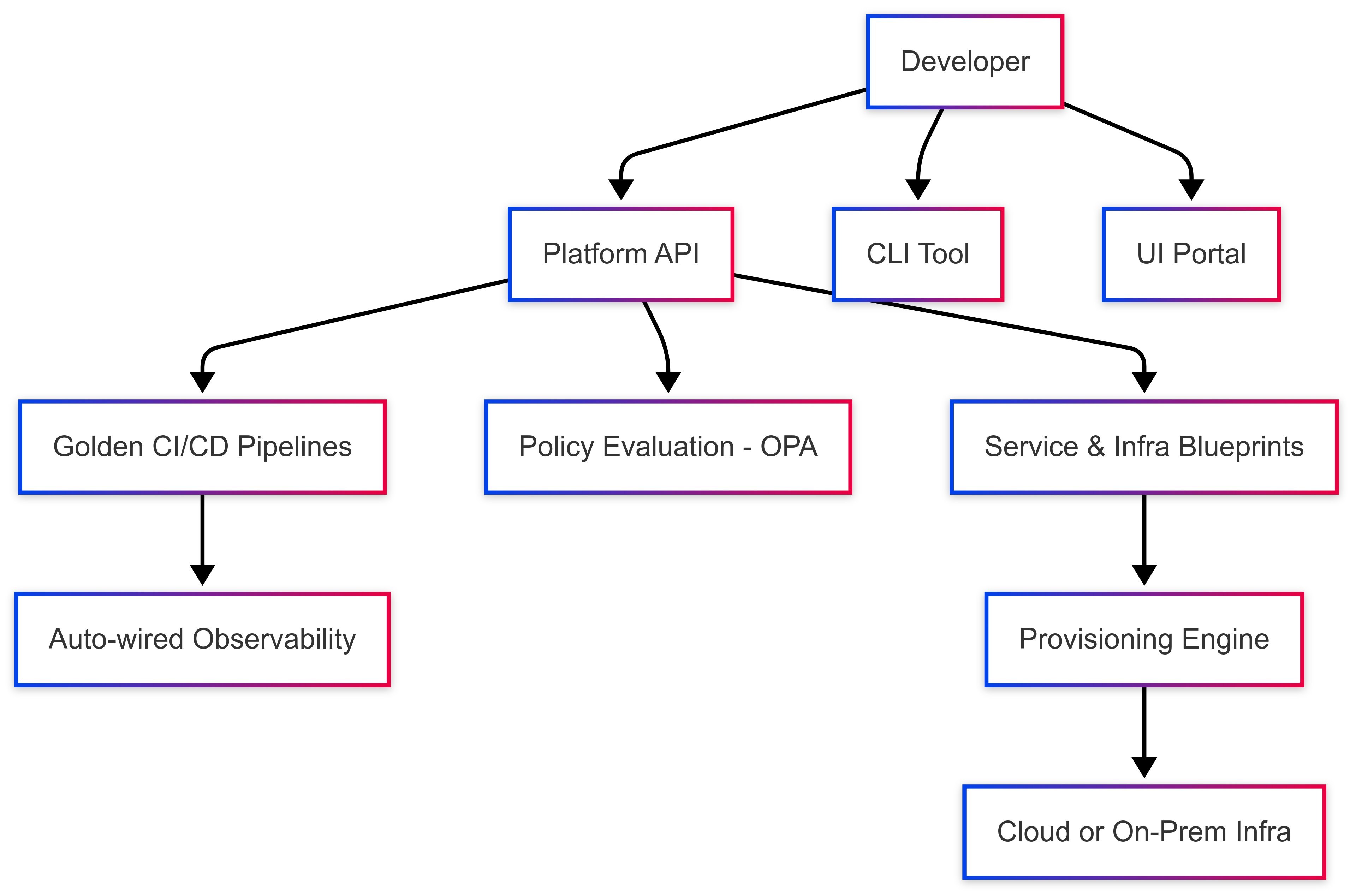
✅ Outcome: Fully automated, compliant, and developer-friendly delivery.
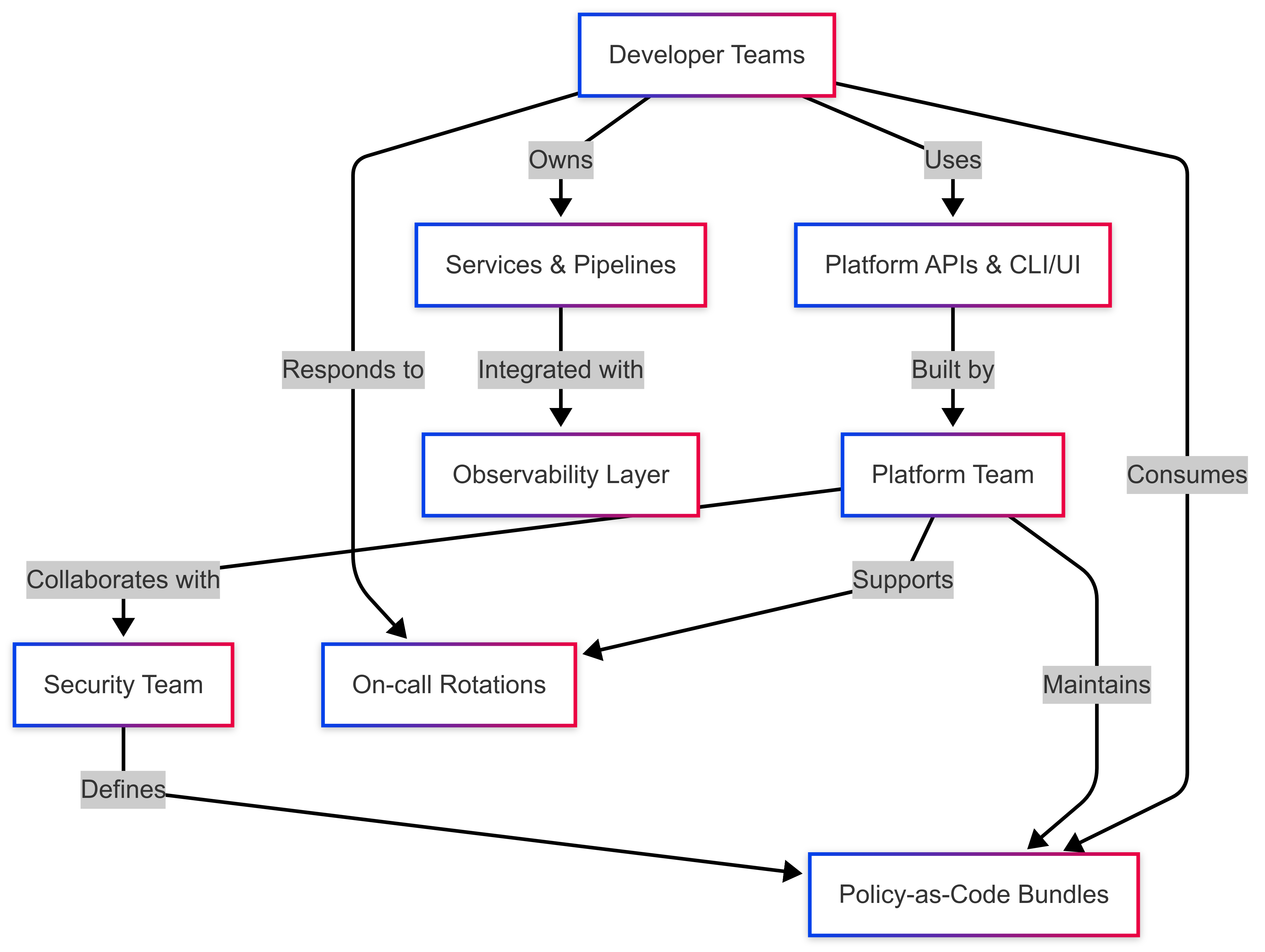
🏗️ 4. Operating Model: People, Ownership, and the Shift Left
This platform capability is not just about technology. It redefines how teams operate, shifting infrastructure responsibilities left and enabling true developer autonomy.
The operating model aligns with modern DevOps principles, but pushes them further by productizing the platform and establishing clear ownership across layers.
🧩 Role-Based Ownership Matrix
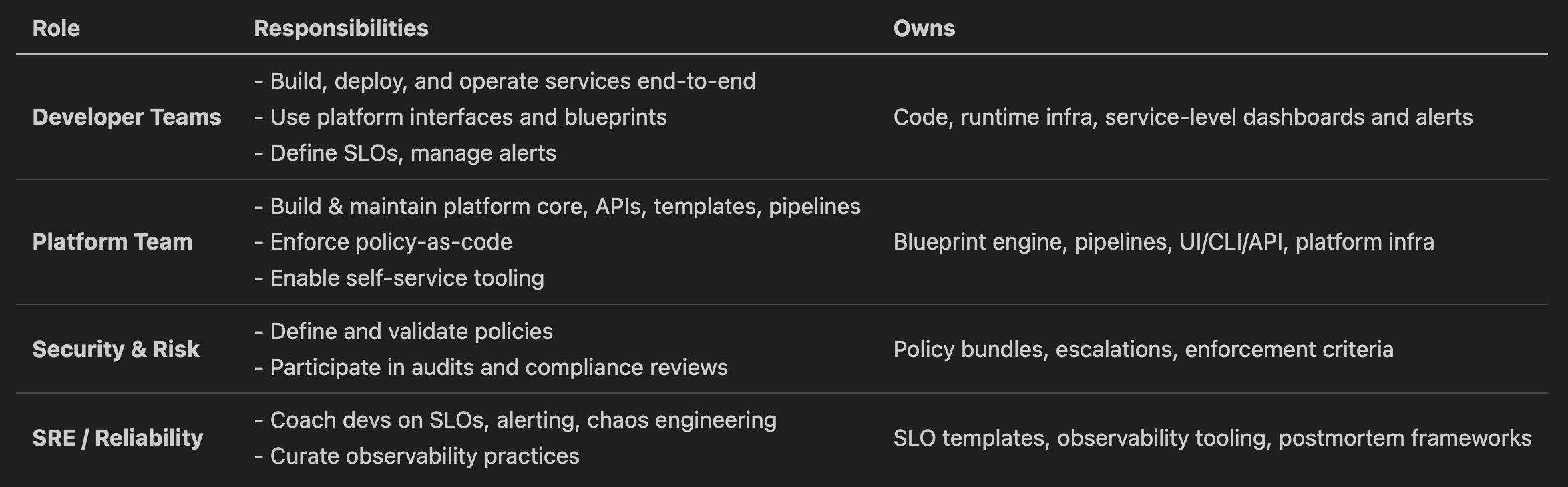
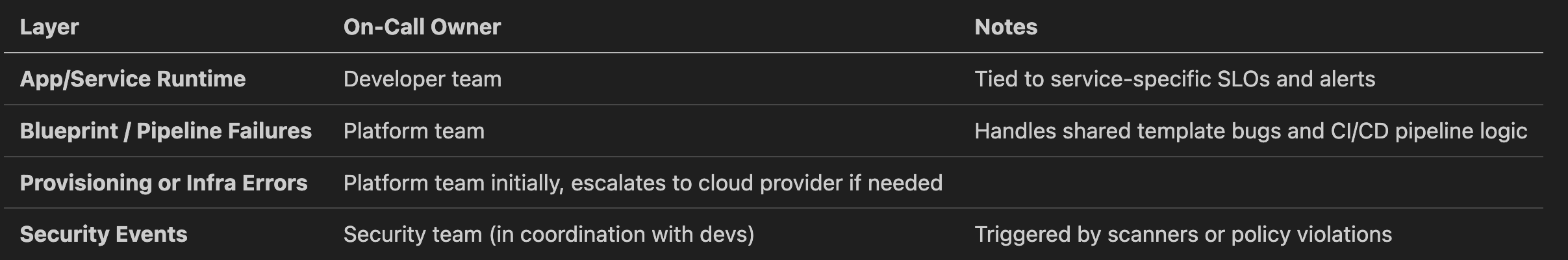
🛎️ On-Call and Incident Ownership
🔧 Proactive Support Model
-
Office Hours: Regular sessions hosted by platform team for onboarding and problem-solving
-
Slack Channels: #ask-platform, #policy-help, #blueprint-feedback
-
Embedded Champions: Platform team members embedded temporarily with key product squads during early adoption
🧠 Platform as a Product: Ways of Working
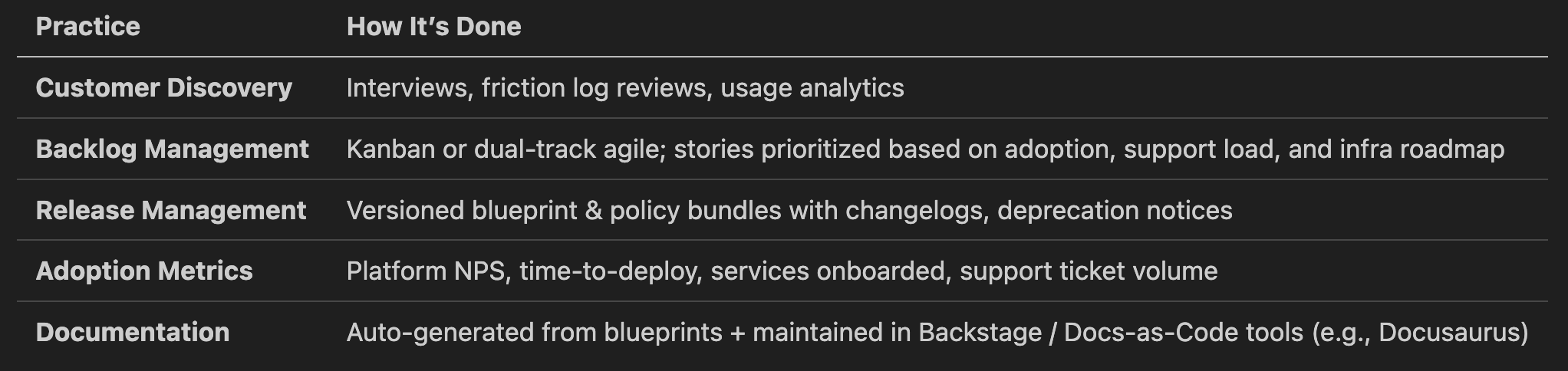
RACI Model for Platform Interactions
🔐 5. Governance & Compliance
In a modern platform model, governance cannot be an afterthought — but it also shouldn’t be a blocker. The platform must enforce compliance and security while preserving developer velocity.
🧱 Section 1: Governance Enforcement Layers
The platform introduces governance through three key enforcement layers:
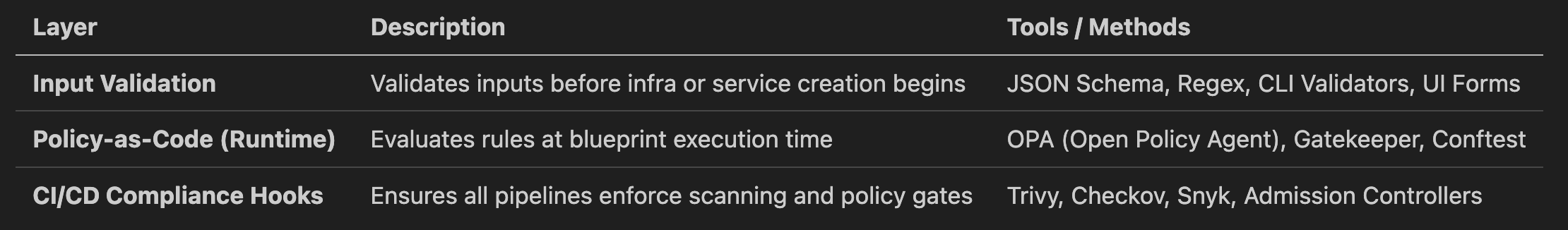
These layers combine to deliver “trust, but verify” workflows — codified, testable, and enforced consistently.
📁 Section 2: Policy Bundle Design
Policies are organized as modular bundles and managed just like application code — versioned, tested, and deployed with changelogs.
📦 Sample Folder Structure
policy-bundle/
├── terraform/
│ ├── enforce-encryption.rego
│ ├── restrict-instance-types.rego
├── kubernetes/
│ ├── restrict-host-paths.rego
│ └── enforce-resource-limits.rego
├── cicd/
│ ├── block-default-branch-push.yaml
│ └── enforce-security-scan.yaml
├── metadata/
│ ├── version.json
│ └── policy-owners.yamlThis structure allows teams to release policy updates safely and revert changes when needed.
🔄 Section 3: Governance Lifecycle
Policy management is not static. It requires a structured lifecycle:
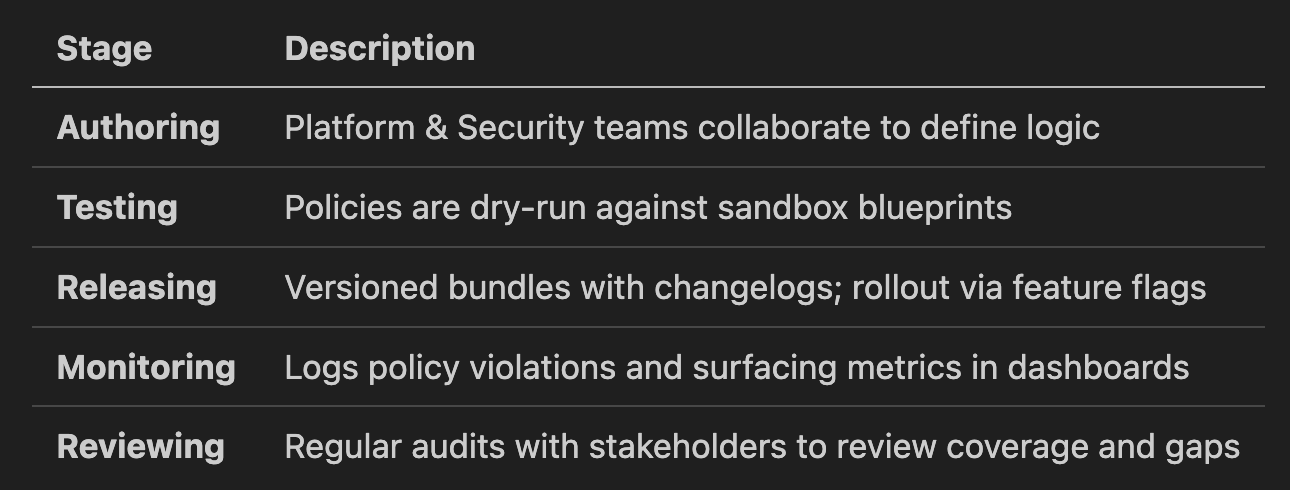
This gives teams confidence that governance will scale with their workloads.
Policy Enforcement Flow
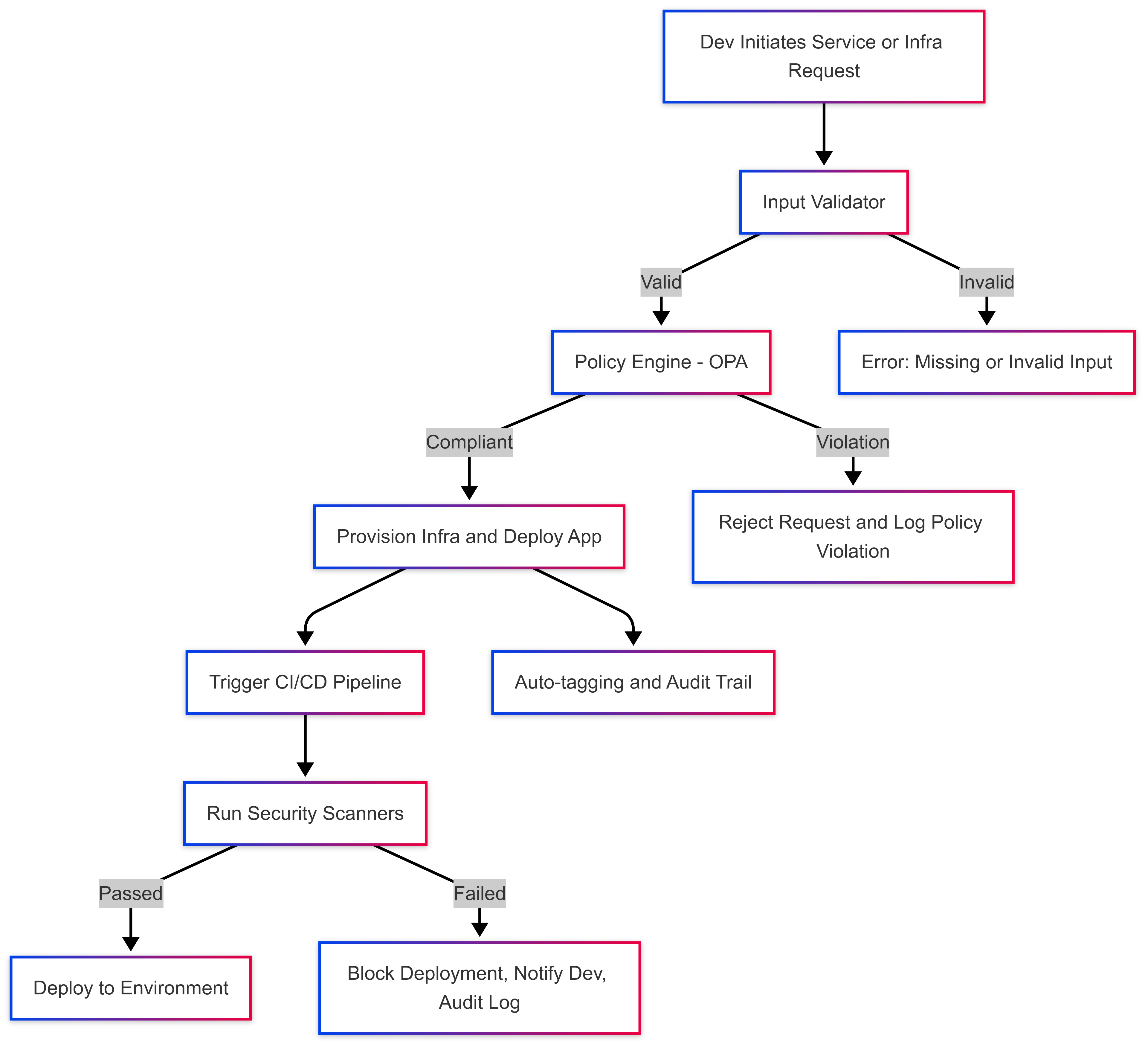
✅ This flow enforces policies without blocking workflows. Developers get fast feedback. Security teams get visibility. Auditors get logs.
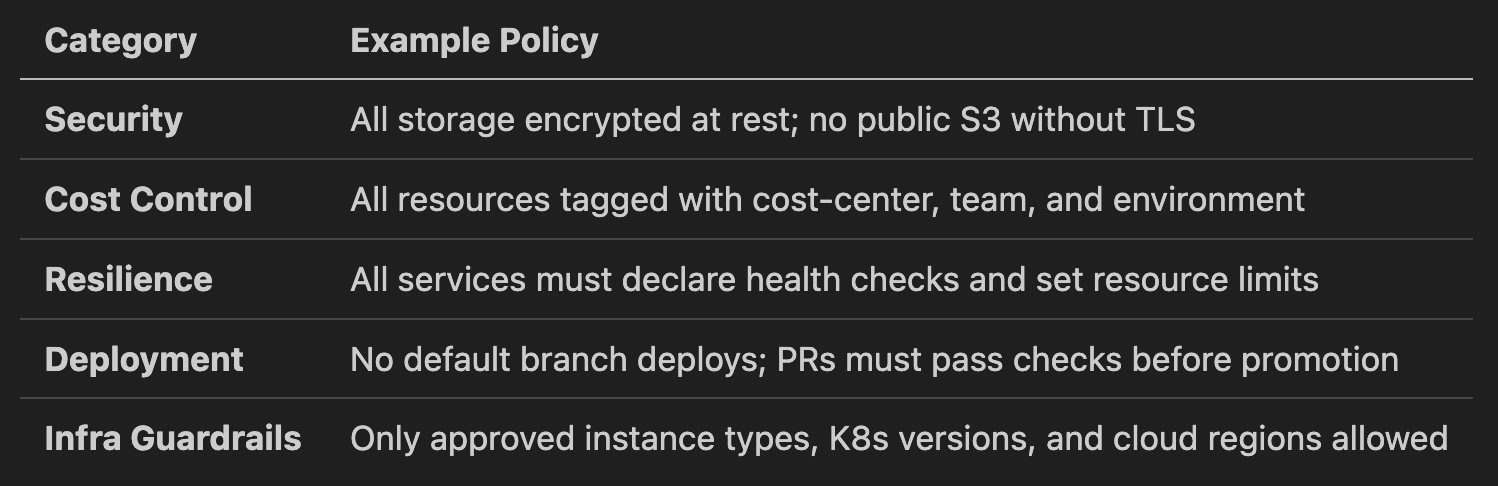
🛡️ Common Policies You Might Enforce
🚀 Part 6: Capability Evolution Roadmap
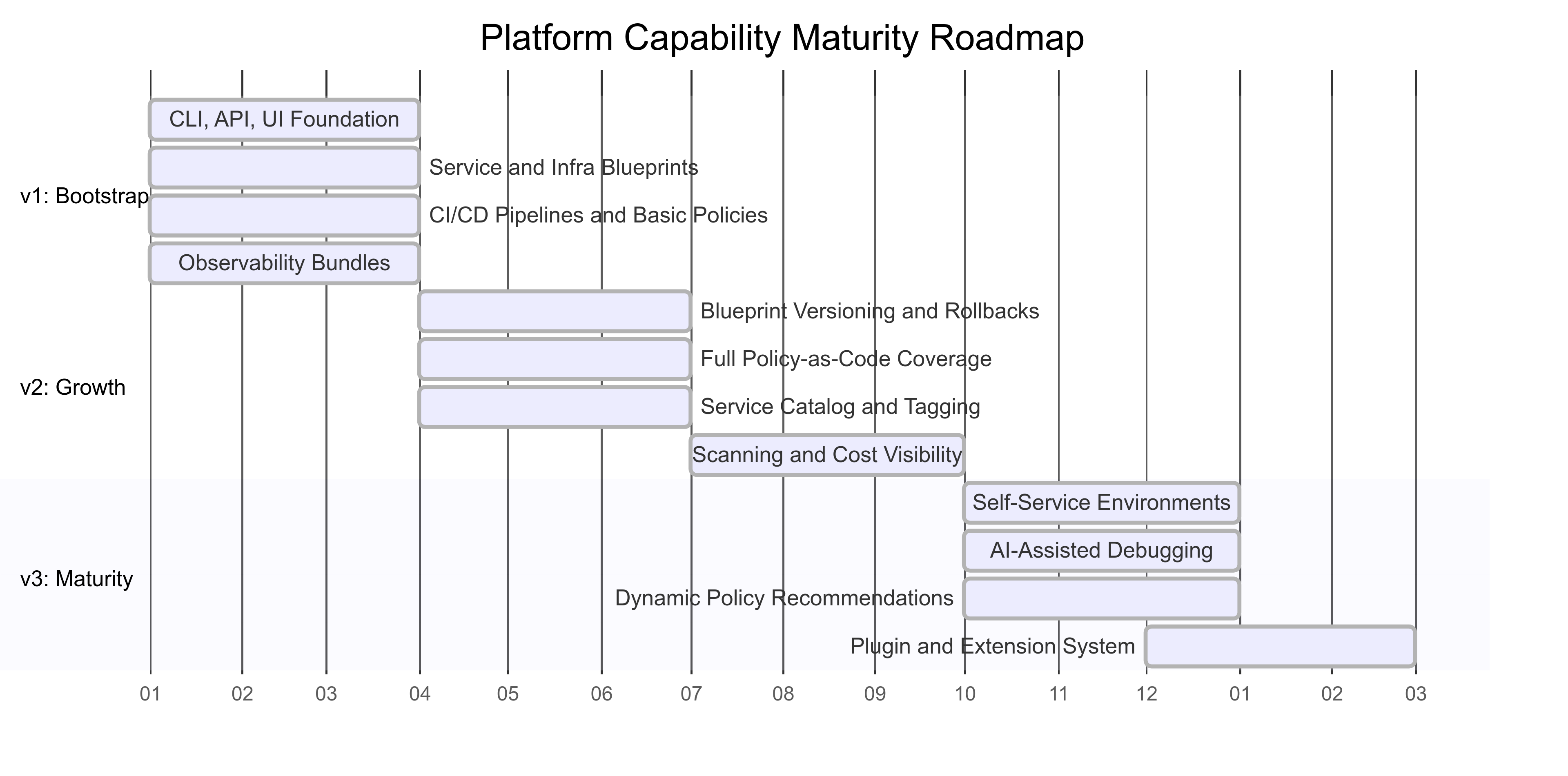
The platform is designed to evolve through three maturity phases — each expanding capability, adoption, and value. This roadmap supports iterative rollout, early feedback loops, and increasing automation.
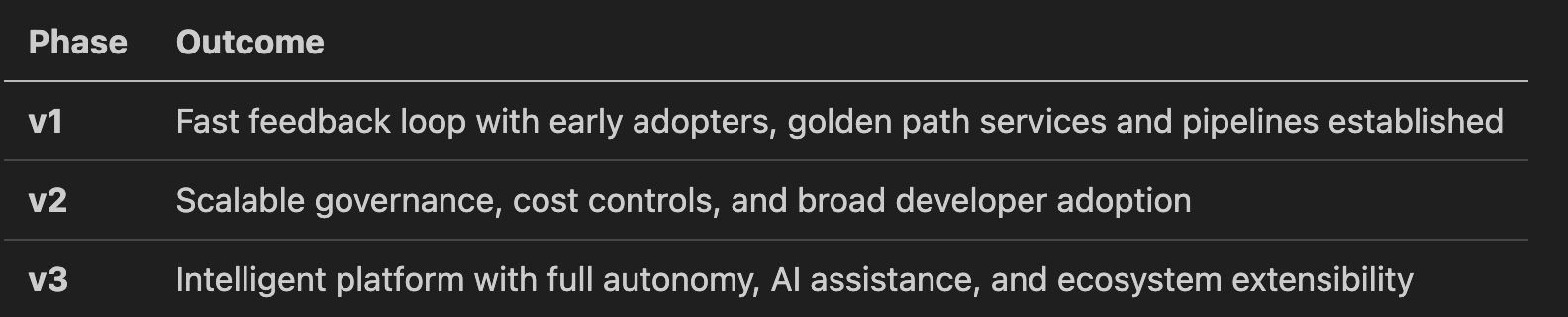
🟢 v1 – Bootstrap Phase: Laying the Foundation
🎯 Goal
Establish core self-service platform functionality for a small group of early adopters.
✅ Capabilities
-
CLI, API, and UI foundation with auth and RBAC
-
Golden-path service scaffolding (e.g., REST API, event processor, batch jobs)
-
Infra blueprints for common resources (PostgreSQL, S3, K8s namespace)
-
Standardized CI/CD pipeline templates
-
Basic policy enforcement (input validation + P0 policy-as-code)
-
Basic observability bundles (logging + metrics)
👥 Target Audience
-
Pilot developer teams with strong maturity
-
Platform team + embedded SRE/Security
📏 Metrics
-
Time to first successful deployment
-
% of pilot services onboarded to platform
-
Initial dev feedback (surveys, platform NPS, onboarding friction logs)
🟡 v2 – Growth Phase: Scaling Adoption and Governance
🎯 Goal
Expand adoption across more teams and embed full-stack governance and cost controls.
✅ Capabilities
-
Versioned blueprints with changelogs and rollback support
-
CI/CD enhancements: multi-env pipelines, canary deploys, parallel test orchestration
-
Service catalog with ownership metadata, tagging, and dependency graphing
-
Full-stack policy enforcement (IaC, CI/CD, K8s, runtime)
-
Security scanning integrated into pipelines (SAST, container scanning, IaC scanning)
-
Cost visibility tooling and auto-tagging per team, project, and environment
-
Onboarding experience: documentation portal, platform training kits, internal dev advocacy
👥 Target Audience
-
All engineering teams across business units
-
Platform champions and embedded product engineers
-
Central compliance, security, and FinOps stakeholders
📏 Metrics
-
% of services onboarded to platform
-
Policy compliance success rate (violations vs. total executions)
-
Mean time to deploy (MTTD) for teams on the platform
-
Developer Net Promoter Score (dNPS)
🔵 v3 – Maturity Phase: Autonomous, AI-Assisted Platform
🎯 Goal
Enable developer autonomy at scale through AI, intelligent automation, and extensibility.
✅ Capabilities
-
Self-service ephemeral environments (e.g., branch previews, feature-specific staging)
-
AI copilots for pipeline debugging, blueprint recommendations, and root cause triage
-
Dynamic policy recommendations based on usage trends and team patterns
-
Intelligent alerting (auto-suppression, deduplication, escalation routing)
-
Advanced cost optimization (team-level insights, anomaly detection)
-
Plugin framework for custom extensions (e.g., team-specific blueprints, validations)
👥 Target Audience
-
Entire engineering organization
-
Central platform, security, and ops teams
-
External/internal developer ecosystems (e.g., for partner APIs)
📏 Metrics
-
% of incidents auto-resolved via platform tooling
-
of custom blueprints created and extended
-
SLA compliance (uptime, latency) across platform-managed services
-
Platform cost efficiency (per developer, per service)
Capability Maturity Roadmap
✅ Summary of Strategic Outcomes by Phase
🧰 Part 7: Tech Stack Overview
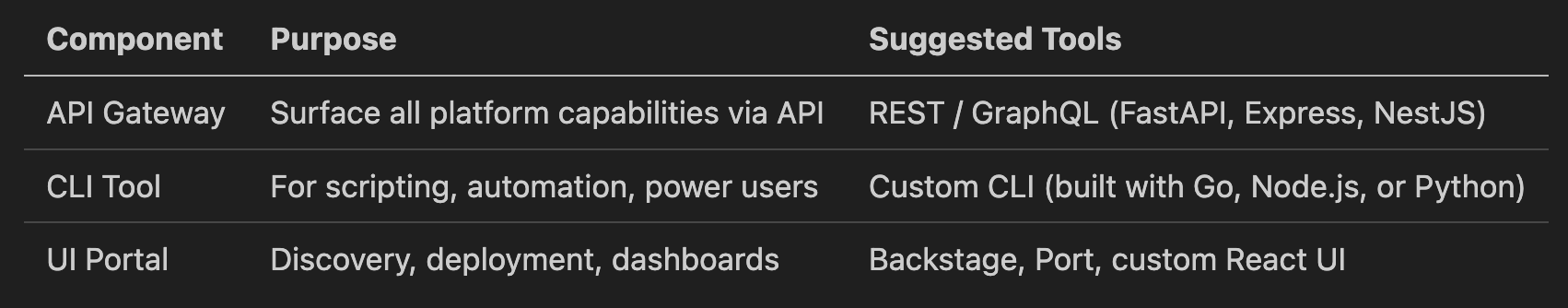
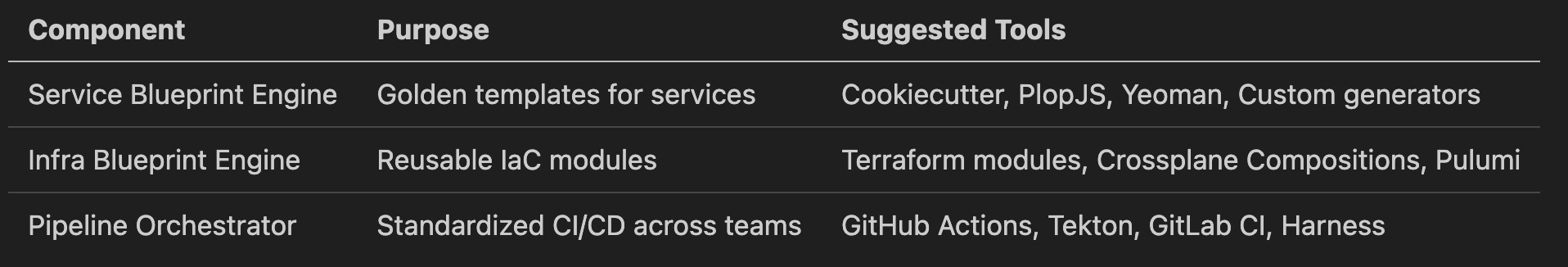
This section summarizes recommended technologies and tools to implement the platform layers described earlier. These are composable, open-source-friendly, and battle-tested in modern cloud-native environments.
🧩 1. Developer Interface Layer
🧱 2. Core Platform Services
🔐 3. Governance & Policy Layer
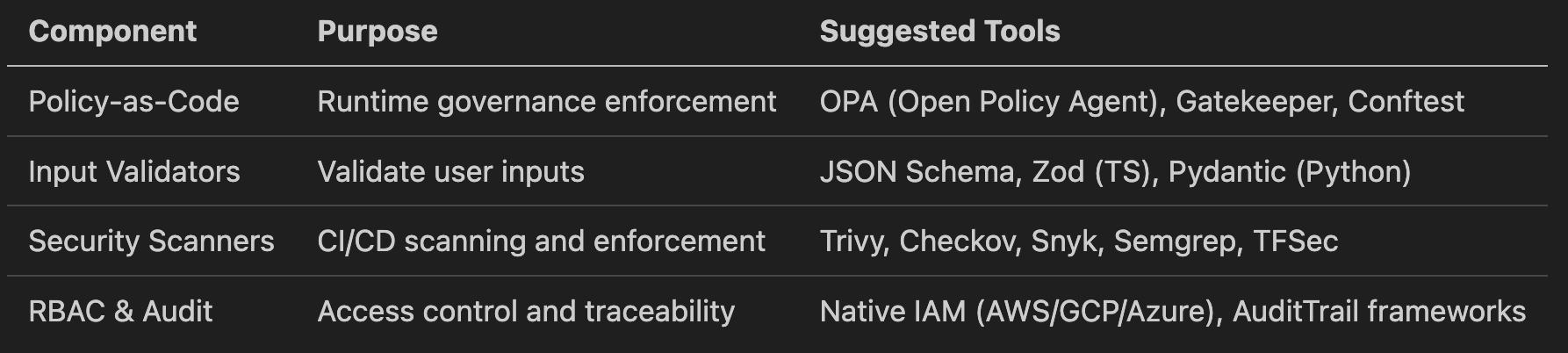
☁️ 4. Provisioning & Runtime Layer
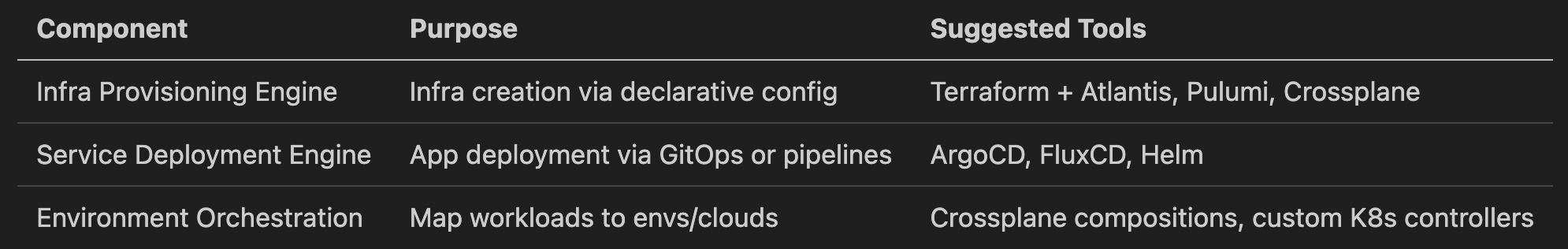
📈 5. Observability & Cost Intelligence
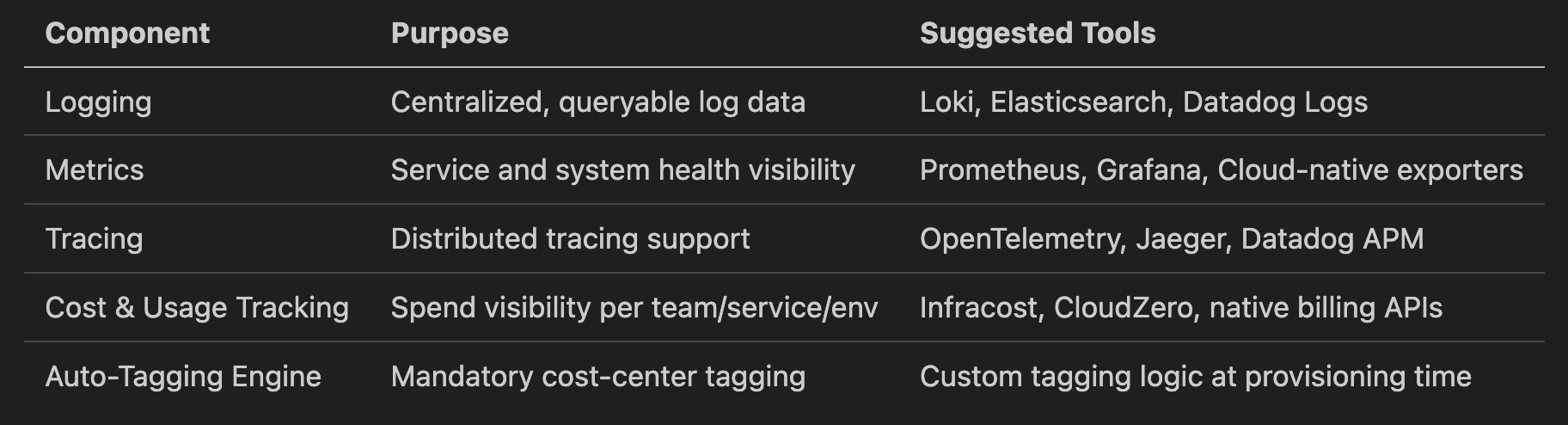
⚙️ 6. Developer Productivity & Extensions
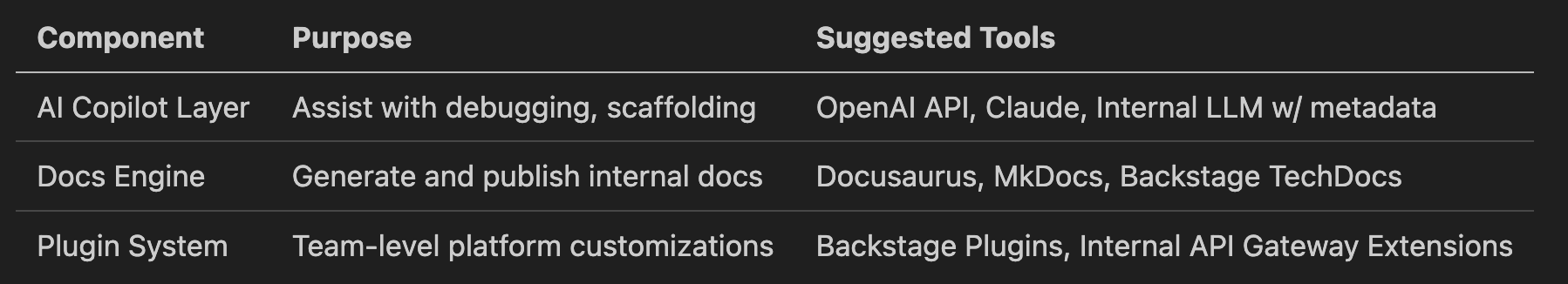
Tech Stack Overview
🎯 Conclusion: Building for the Future
Platform Engineering is not a trend — it’s a strategic capability that separates high-performing digital-first organizations from the rest. What you’ve read here isn’t theoretical. It’s drawn from patterns that have worked at scale — from hyperscalers like Amazon to modern platform-native startups.
By unifying the developer experience, codifying governance, and shifting infrastructure into product form, your teams move faster, ship safer, and operate with less friction.
As you begin (or scale) your platform journey, ask yourself:
-
Are your developers spending more time wiring pipelines than writing business logic?
-
Are security and compliance slowing you down — or built into the path of least resistance?
-
Is your platform an enabler — or just another toolchain to navigate?
✅ The opportunity: Treat the platform like a product. Empower developers as customers. Build once, use everywhere.
🚀 Call to Action
Whether you’re a CTO, platform lead, or engineering leader:
-
Audit your current platform footprint. Identify duplication, friction, and gaps.
-
Design for self-service. Every manual handoff is a future bottleneck.
-
Start with v1 — but design for v3. Build iteratively, but keep the vision bold.
-
Don’t build in a vacuum. Embed platform champions in teams. Use feedback as a compass.
-
Track adoption like a product. NPS, usage, time-to-deploy — these are your KPIs.
This is how you enable autonomy at scale. This is how you create leverage for your organization. The best platforms don’t just reduce toil. They unlock potential.